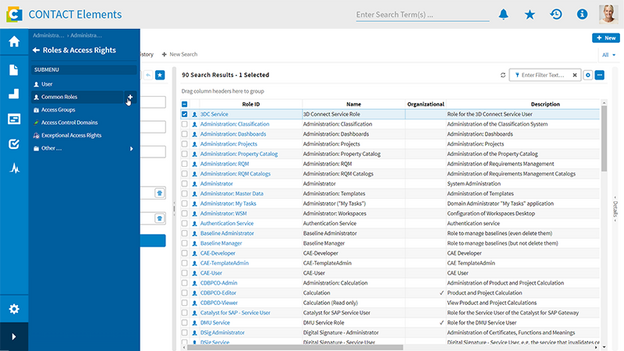
Securely and flexibly control data access with role-based access control
In a globally connected work environment, companies increasingly face challenges in protecting their knowledge and know-how. Complex structures in organizations, projects, and responsibilities, with frequent adjustments, complicate the management of access rights. At the same time, sensitive data must be specially protected, and legal requirements and compliance guidelines must be adhered to. With the features of CONTACT Elements for Roles & Access Rights, you reliably meet these requirements – without high manual effort and risks.
Your benefits
- Reliably protect knowledge and know-how through access regulation with a role concept
- Implement specifications and security guidelines reliably
- Automatically adjust rights profiles with a dynamic rights system
- Automatically determine and adjust protection classes based on document properties
- Ensure traceability and compliance through audit trails

Protect knowledge and know-how with a role concept
With Roles & Access Rights, you control access to all data throughout the product and project lifecycle. The flexible role concept enables the easy definition and maintenance of precise permission profiles. Access rights are directly derived from assigned roles: For example, the 'Planner' role can create and edit work plans, while the 'Public' role only has read-only access. This control is possible not only at the object level, but also for individual attributes of the object. Through general, user- or context-specific roles and grouping, organizational structures can be precisely mapped. In this way, you protect corporate knowledge and intellectual property and consistently enforce security policies.
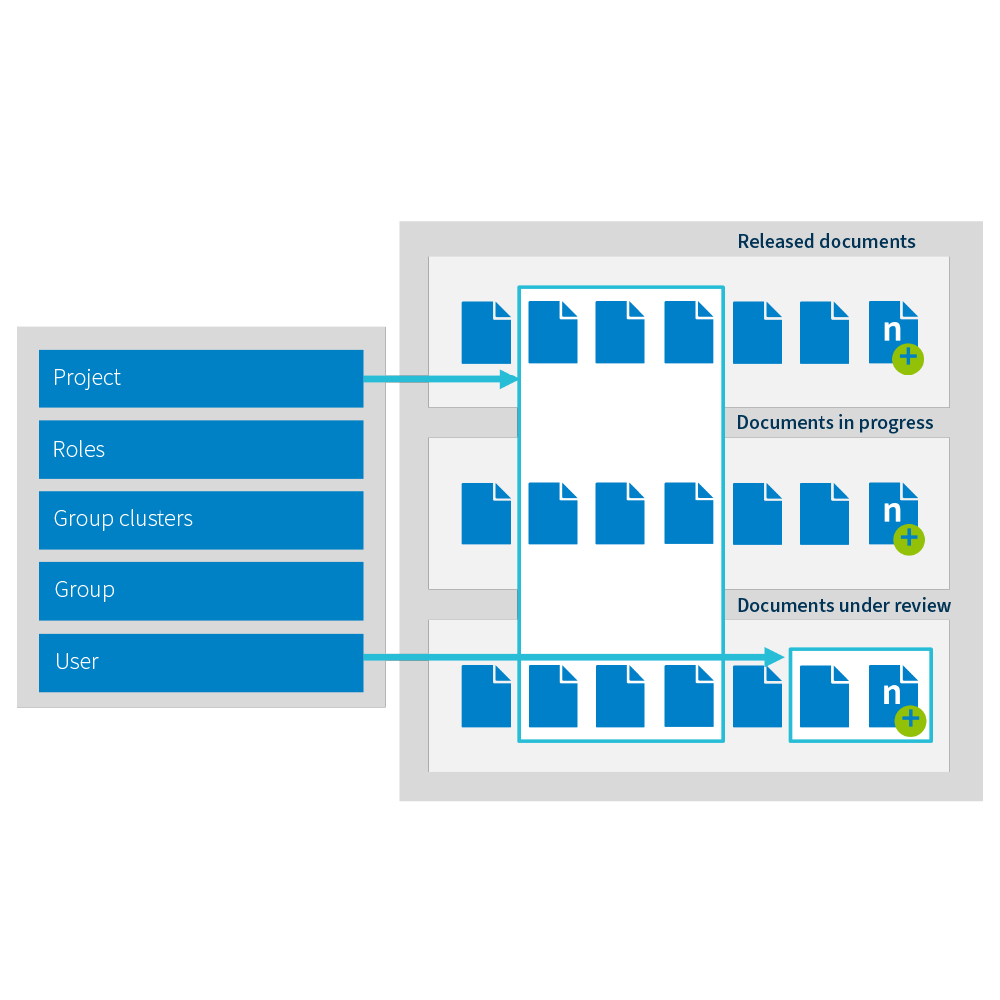
With Roles & Access Rights, you control access to all data throughout the product and project lifecycle. The flexible role concept enables the easy definition and maintenance of precise permission profiles. Access rights are directly derived from assigned roles: For example, the 'Planner' role can create and edit work plans, while the 'Public' role only has read-only access. This control is possible not only at the object level, but also for individual attributes of the object. Through general, user- or context-specific roles and grouping, organizational structures can be precisely mapped. In this way, you protect corporate knowledge and intellectual property and consistently enforce security policies.
Automatically adapt rights profiles with a dynamic rights system
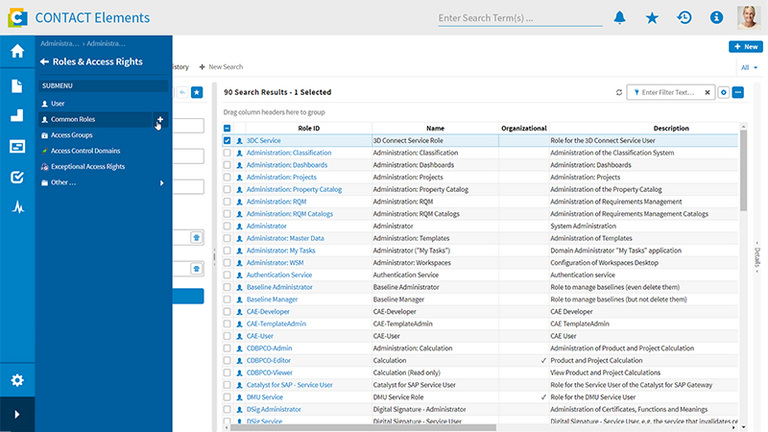
The dynamic rights system of Roles & Access Rights ensures that access rights are correctly assigned at all times and without manual effort. Organizational changes – such as project, location, or department changes – are automatically considered, and rights are adjusted accordingly. Similarly, the system determines protection classes based on document properties like confidentiality, development maturity level, or status, and updates them immediately upon changes. This way, you reliably protect sensitive data and support collaboration through company-wide, always up-to-date rights profiles.
Automatically adapt rights profiles with a dynamic rights system
The dynamic rights system of Roles & Access Rights ensures that access rights are correctly assigned at all times and without manual effort. Organizational changes – such as project, location, or department changes – are automatically considered, and rights are adjusted accordingly. Similarly, the system determines protection classes based on document properties like confidentiality, development maturity level, or status, and updates them immediately upon changes. This way, you reliably protect sensitive data and support collaboration through company-wide, always up-to-date rights profiles.
The dynamic rights system of Roles & Access Rights ensures that access rights are correctly assigned at all times and without manual effort. Organizational changes – such as project, location, or department changes – are automatically considered, and rights are adjusted accordingly. Similarly, the system determines protection classes based on document properties like confidentiality, development maturity level, or status, and updates them immediately upon changes. This way, you reliably protect sensitive data and support collaboration through company-wide, always up-to-date rights profiles.
Ensure traceability and compliance through Audit Trails
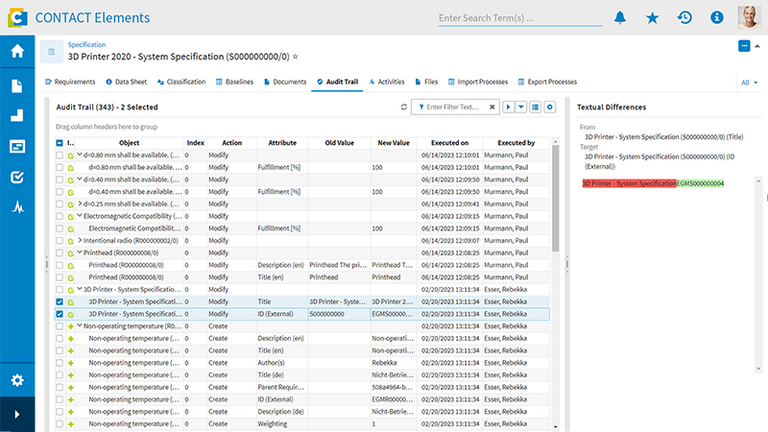
Crucial for effective access control is the traceability of all activities. With Roles & Access Rights, permissions are clearly defined and consistently implemented. Additionally, Audit Trails document all data access and changes to roles or rights in an audit-proof manner. Your company thus fulfills internal requirements, as well as external compliance requirements (e.g., GDPR, ISO 27001, or industry-specific standards). In the event of an audit, you can easily meet all proof obligations at any time.
Ensure traceability and compliance through Audit Trails
Crucial for effective access control is the traceability of all activities. With Roles & Access Rights, permissions are clearly defined and consistently implemented. Additionally, Audit Trails document all data access and changes to roles or rights in an audit-proof manner. Your company thus fulfills internal requirements, as well as external compliance requirements (e.g., GDPR, ISO 27001, or industry-specific standards). In the event of an audit, you can easily meet all proof obligations at any time.
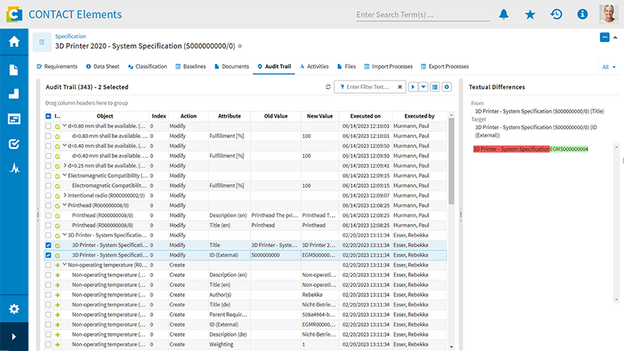
Crucial for effective access control is the traceability of all activities. With Roles & Access Rights, permissions are clearly defined and consistently implemented. Additionally, Audit Trails document all data access and changes to roles or rights in an audit-proof manner. Your company thus fulfills internal requirements, as well as external compliance requirements (e.g., GDPR, ISO 27001, or industry-specific standards). In the event of an audit, you can easily meet all proof obligations at any time.
How to design secure IT environments

IT security is complex. Defending against cyberattacks is just one facet. In our White Paper "IT security for companies", you learn what you need to consider when designing your IT environment.
How to design secure IT environments
IT security is complex. Defending against cyberattacks is just one facet. In our White Paper "IT security for companies", you learn what you need to consider when designing your IT environment.

IT security is complex. Defending against cyberattacks is just one facet. In our White Paper "IT security for companies", you learn what you need to consider when designing your IT environment.
Related Elements
Ensure reliable IT operations
Robust IT security architecture for reliable operation
Simple and secure user management and authentication
Reliable access protection through personalized logins and multifactor authentication (MFA)
Comprehensive encryption for secure data transmission
Confidentiality, authenticity, and integrity of data
Document the lifecycle of documents and other PLM objects seamlessly
Trace the lifecycle of documents and PLM objects seamlessly with Audit Trails
Easily compile regulatory-relevant documents into folders
Ensure traceability with digital lifecycle records and improve the use of products and systems
Organize and utilize know-how enterprise wide
Make all important documents available on every workstation
Save valuable time when searching for documents
Protect valuable know-how
Speed up test and release processes
Comply with regulatory requirements more easily
Further information
Would you like to learn more about this topic? Choose from one of the following information offers.