IT security is of existential importance – and a prerequisite for successful digitization
IT security is essential for digital transformation. According to Bitkom, cyberattacks caused a total loss of 266 billion euros to the German economy in 2024. Companies need a resilient IT security architecture to protect themselves. Many topics are relevant in this context, including data and intellectual property security, compliance requirements, verification obligations for product liability or the mapping of role and permission rights in user management. CONTACT Elements allows you to fulfil these requirements. Proven security concepts and powerful software solutions enable secure end-to-end digitalization of your business processes.
Your benefits
- Robust IT security architecture for reliable operation
- Simple and secure user management and authentication
- Reliable access protection through personalized logins and multifactor authentication (MFA)
- Comprehensive encryption for secure data transmission
- Confidentiality, authenticity, and integrity of data
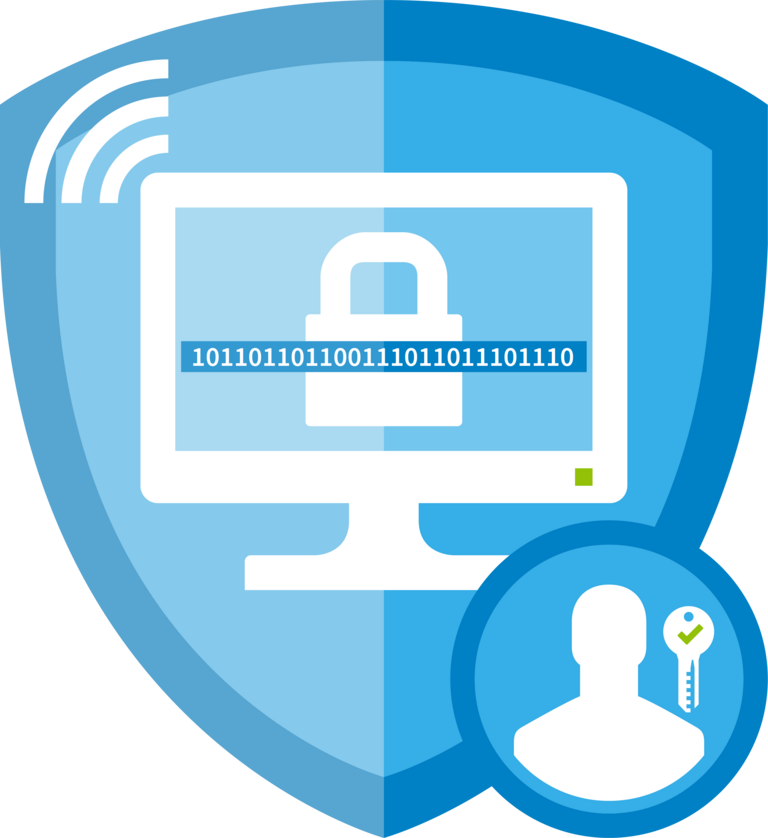
Robust IT security architecture for reliable operation

CONTACT Element’s security architecture is based on current standards and preconfigurations. These ensure secure system operation and provide protection against cyberattacks. Our reliable incident management process allows fast responses to security incidents. With its component architecture and transparent configuration and software change processes, Elements also helps organizations to meet IT security requirements and document changes. Event logging and monitoring interfaces assist with integration into an existing information security management system (ISMS).
Robust IT security architecture for reliable operation
CONTACT Element’s security architecture is based on current standards and preconfigurations. These ensure secure system operation and provide protection against cyberattacks. Our reliable incident management process allows fast responses to security incidents. With its component architecture and transparent configuration and software change processes, Elements also helps organizations to meet IT security requirements and document changes. Event logging and monitoring interfaces assist with integration into an existing information security management system (ISMS).

CONTACT Element’s security architecture is based on current standards and preconfigurations. These ensure secure system operation and provide protection against cyberattacks. Our reliable incident management process allows fast responses to security incidents. With its component architecture and transparent configuration and software change processes, Elements also helps organizations to meet IT security requirements and document changes. Event logging and monitoring interfaces assist with integration into an existing information security management system (ISMS).
Secure user management and authentication
CONTACT Elements enables user management and authentication directly in our platform or through the integration of an existing Identity & Access Management (IAM) system. Elements supports secure login methods like passwordless single sign-on as well as the configuration of flexible password rules to meet compliance requirements. Additionally, multifactor authentication (MFA) secures access to systems, networks and databases as well as physical sites. Use standardized interfaces to integrate IAM solutions such as Microsoft Entra or Keycloak into your IT landscape. You benefit from smooth IT processes and reduced administration costs.
Secure user management and authentication
CONTACT Elements enables user management and authentication directly in our platform or through the integration of an existing Identity & Access Management (IAM) system. Elements supports secure login methods like passwordless single sign-on as well as the configuration of flexible password rules to meet compliance requirements. Additionally, multifactor authentication (MFA) secures access to systems, networks and databases as well as physical sites. Use standardized interfaces to integrate IAM solutions such as Microsoft Entra or Keycloak into your IT landscape. You benefit from smooth IT processes and reduced administration costs.
CONTACT Elements enables user management and authentication directly in our platform or through the integration of an existing Identity & Access Management (IAM) system. Elements supports secure login methods like passwordless single sign-on as well as the configuration of flexible password rules to meet compliance requirements. Additionally, multifactor authentication (MFA) secures access to systems, networks and databases as well as physical sites. Use standardized interfaces to integrate IAM solutions such as Microsoft Entra or Keycloak into your IT landscape. You benefit from smooth IT processes and reduced administration costs.
Reliable encryption for secure data transmission
Users and the system communicate via the tap-proof HTTPS protocol. Similarly, data exchange between system components is also protected by HTTPS transport encryption. CONTACT Elements uses the proven Transport Layer Security (TLS) encryption protocol to secure data during transmission. The platform utilizes the current TLS 1.3 standard with Perfect Forward Secrecy (PFS) and the Authenticated Encryption with Associated Data (AEAD) method. AES-GCM encryption is used for this. It guarantees the confidentiality, authenticity and integrity of the data. The HTTP Strict Transport Security (HSTS) mechanism protects your company from threats such as downgrade attacks or session hijacking.
Users and the system communicate via the tap-proof HTTPS protocol. Similarly, data exchange between system components is also protected by HTTPS transport encryption. CONTACT Elements uses the proven Transport Layer Security (TLS) encryption protocol to secure data during transmission. The platform utilizes the current TLS 1.3 standard with Perfect Forward Secrecy (PFS) and the Authenticated Encryption with Associated Data (AEAD) method. AES-GCM encryption is used for this. It guarantees the confidentiality, authenticity and integrity of the data. The HTTP Strict Transport Security (HSTS) mechanism protects your company from threats such as downgrade attacks or session hijacking.

Security at the highest level
The development and operation of cloud products based on CONTACT Elements fulfil the strict requirements of the ISO 27001 standard. This certification confirms that the solutions from CONTACT Software meet the highest security standards and your data is in safe hands with us.
6 criteria for IT security in companies

IT security has many facets. Defending against cyberattacks is just one of them. Learn what you need to consider when designing your IT environment in our White Paper "IT security for companies"!
6 criteria for IT security in companies
IT security has many facets. Defending against cyberattacks is just one of them. Learn what you need to consider when designing your IT environment in our White Paper "IT security for companies"!

IT security has many facets. Defending against cyberattacks is just one of them. Learn what you need to consider when designing your IT environment in our White Paper "IT security for companies"!
Related Elements
Verify objects faster, meet regulatory requirements
Speed up circulation procedures for verification and approval processes
Meet regulatory requirements and improve validity control and process reliability
Organize and utilize know-how enterprise-wide
Make all important documents available on every workstation
Save valuable time when searching for documents
Protect valuable know-how
Speed up test and release processes
Comply with regulatory requirements more easily
Regulate data access, protect know-how
Implement key requirements for know-how protection reliably throughout the entire company
Take advantage of the possibilities offered by a powerful and dynamic rights system
Regulate access to project and product data along your processes based on roles
Ensure validity control with reliable version management
Further Information
Would you like to find out more about this topic? Choose one of the following information offers.

