Collaboration Portal: How to Securely Integrating Other Companies in Your Processes
Today, web-based solutions make it possible to efficiently integrate external partners in your development processes. This speeds up work and makes it more reliable but raises the question of how sensitive data can be protected against unauthorized access, malware and the like. The comprehensive security concept behind CONTACT's Collaboration Portal is state of the art.
Collaboration Portal is a standard component of the CONTACT Elements platform. The web portal connects CIM DATABASE PLM and Project Office users with engineering offices, suppliers and customers. Instead of emailing, the individuals involved work on their CAx data and documents much more efficiently in a shared process and project context.
Access to internal know-how is clearly defined: In the case of external users, it is confined to the workflows initiated and predefined by a company's own internal employees. CONTACT Software has, at the same time, also used possible attack vectors to analyze scenarios that go beyond what is normal and instead involve negligent or willful behavior. The result provides a framework for secure operation and damage control in the event of an attack. The key components of this security architecture are described in the following.
Secure network and server architecture
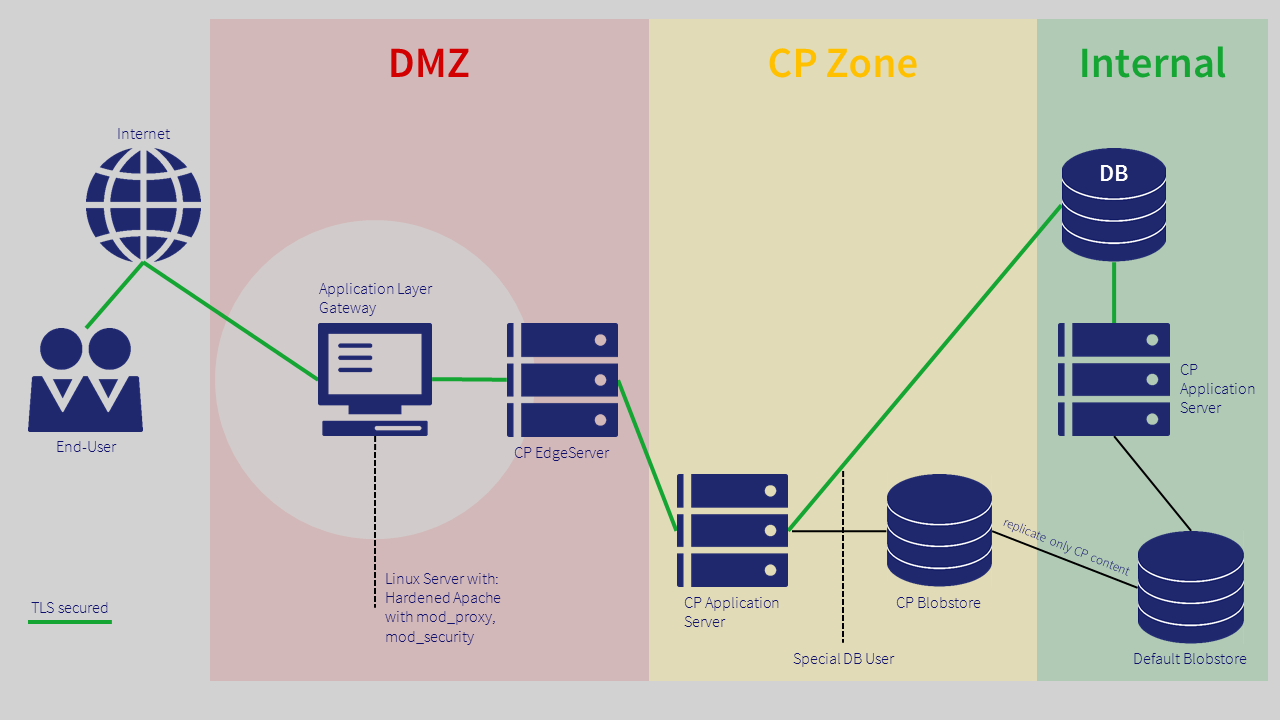
An appropriate network and server architecture is the key requirement for secure operation. The recommendation that we have drawn up provides for three separate network zones and separate application and edge servers for the Collaboration Portal (CP). This creates two additional high-security areas between the Internet and the intranet according to the defense-in-depth principle. Firewalls at every gateway prevent security gaps outside of the defined channels from being exploited.
In the first, demilitarized, zone (DMZ), an application layer gateway receives all requests and at this point filters out any potential attacks. Valid requests are forwarded to the edge server, which in turn is connected to the CP application server in the second network zone.
This "CP zone" contains a dedicated application server for the Collaboration Portal as well as a separate vault. Neither the CP application installed here nor the edge server in the first zone contains development or administration tools.
The CP application server does not have access to internal vaults and uses a database connection with very limited rights. The way in which the firewall is configured means that only the CP vault can communicate with an internal vault. Even if an attack were successful, this measure would prevent additional rights from being acquired and files that have not been approved for the Collaboration Portal from being viewed in this zone.
The internal vault provided for data replication with the CP vault is located in the third network zone. Before data is transferred to the Collaboration Portal, the internal vault checks whether replication of this data is permitted. Only if this is the case, will the data element actually be replicated.
This "CP zone" contains a dedicated application server for the Collaboration Portal as well as a separate vault. Neither the CP application installed here nor the edge server in the first zone contains development or administration tools.
The CP application server does not have access to internal vaults and uses a database connection with very limited rights. The way in which the firewall is configured means that only the CP vault can communicate with an internal vault. Even if an attack were successful, this measure would prevent additional rights from being acquired and files that have not been approved for the Collaboration Portal from being viewed in this zone.
The internal vault provided for data replication with the CP vault is located in the third network zone. Before data is transferred to the Collaboration Portal, the internal vault checks whether replication of this data is permitted. Only if this is the case, will the data element actually be replicated.
Quickly closing security gaps
The application layer gateway mentioned at the beginning is made available in the form of a virtual machine and is always kept up-to-date. If CONTACT releases a new version with security-related patches, it is sufficient to replace the VM and adapt the network configuration to your own network using the hypervisor (e.g. with a virtual network).
CONTACT is setting up a customer Computer Emergency Response Team (CERT service) for its own products. This will allow known security gaps – including those in components not supplied by us – and updates for closing these gaps to be communicated as quickly as possible.
It is expected that the solution components described here will be available in the first quarter of 2017 for CIM DATABASE 11 and Project Office 4.
Summary
The Collaboration Portal is a web-based solution for collaboration with development partners and customers. A combination of measures ensures that it can be used safely.
Only data elements that have been approved for external persons are made available outside of the internal zone – isolated from the main system with the central database. All access in the portal requires authentication, which is authorized in conjunction with the reading and editing permissions granted via the CONTACT permission system. All data transfer operations via the Internet are encrypted using the TLS 1.2 standard (AES GCM).
Security is not a static state and new threats require appropriate countermeasures. CONTACT Element's component architecture and the applications that build on it allow for fast response in the event of a problem and patch management that immediately closes identified security gaps.
Contact person: Michael Schlenker, Senior Software Engineer